B. Set-up in the Administration Portal
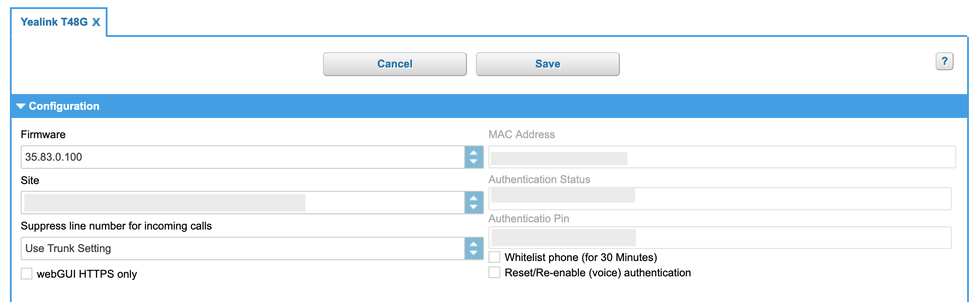
In order to authenticate the phone during its initial provisioning, a special "Phone Authentication PIN" (PAP) is required to provide two-factor authentication for the device. This PAP is obtained from the admin portal under the device settings.
Setup of phones
New devices are created in the admin portal the same way as before. Upon creation, a unique 6-digit PAP is generated. This PAP is valid until the device has been fully provisioned. Once successfully authenticated, the PAP is no longer required.
During the this whole process, the device can be in either of the following three authentication states:
| State | Description |
| Authentication needed | The phone has been set up but has not yet successfully authenticated |
| Authentication failed | The phone is temporarily blocked from authentication and will not accept any PAP |
| Authentication blocked | The phone is permanently blocked form authentication and will not accept any PAP |
| Authentication successful | The phone has been successfully authenticated and fully provisioned |
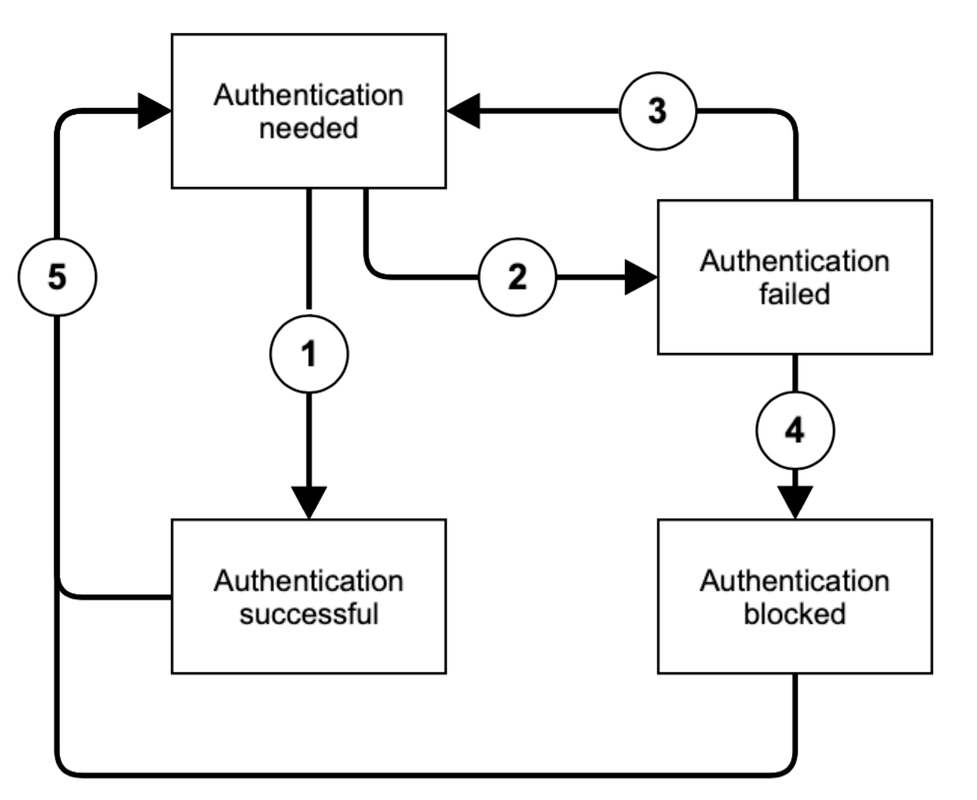
When a new device has been added into the admin portal, its state is initially "authentication needed". In that state, authentication via PAP is required if the phones public IP address has not been added to the whitelist. Upon successful authentication, the state transitions to "authentication successful" (1). Once successfully authenticated, the PAP is no longer required. In case the authentication failed three times in a row, the state traditions automatically form "authentication needed" to "authentication failed" (2). The state will automatically transition back to "authentication needed" after 30 minutes (3). Upon multiple unsuccessful authentication attempts, the state transitions to "authentication blocked" (4) which permanently blocks this phone from additional authentication attempts. In either of these states, the state can manually be reset back to "authentication needed" (5) by resetting the PAP. Therefore, the admin portal provides two actions, which are available in any state:
| Action | Description |
| Suspend Authentication | Explicitly disable any authentication requirements for the particular device for 30 minutes. |
| Reset Authentication | Invalidated the current authentication and immediately generates a new PAP. |
If the device loses its configuration or has been reset to factory defaults, the reset authentication action must be executed in order to generate a new PAP and authenticate the device again.
IP Whitelisting
Permanent whitelisting
For devices that are to be operated from a location that uses a static public IP address, it is possible to whitelist the public IP (as trusted) in the admin portal. The NFON platform will then no longer require authentication using the PAP for all provisioning requests coming from that IP address. The whitelist accepts either single IPv4 addresses (xxx.xxx.xxx.xxx) or IP Ranges in CIDR notation (xxx.xxx.xxx.xxx./yyy). It can be configured in the admin portal “Administration” > “Profile” > "Technical Details".
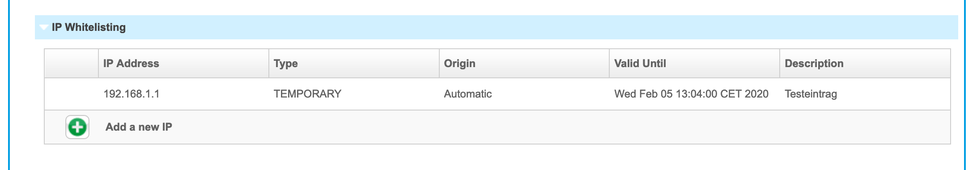
Temporary whitelisting
Upon successful authentication of a device using the PAP, the NFON platform will automatically add the public IP address of the network it received the provisioning request from to a temporary whitelist. The IP address will remain whitelisted for a period of 8 hours from this moment. If new or existing devices are successfully provisioned during this period, the period is extended continuously for a further 8 hours. This mechanism is meant to simplify the provisioning process for new customers or sites, or for when a static IP address is not available or yet known.
CSV Export
It is possible to export a list of all devices from the admin portal, as a CSV file. This file contains the vendor, type, MAC address, creation date, site as well as the authentication state. In case the device is not yet successfully authenticated, the file also contains the PAP for that device. This is done in the admin portal "Administration" > "Batch Import/Export"